TURN OFF YOUR
CELL PHONE
EVERYONE IS LISTENING
By
Søren Nielsen
2019

I have been asked to share what I know about cell phones and the equipment they use, along with the cell phone.
This message has been broadcast worldwide, on all media, on the underground site, and on "The Deep Dark Web"
I have to admit that I didn't what do it, because I use many of the programs myself, when I need to find someone or see and hear what they are talking about.
Now I know 100 percent, that there is sits some one out there, and says that it can not be done, for I can only say,
"If you just need to knew what they can do with your cell phone, then you would never use a cell phone again".
I have been working with mobile telephony for more than 20 years, and I was one of the first in my job to get a mobile phone, if you can call it, a battery so big you almost had to have a backpack on, but could only keep 30 minutes of talk time.
But then things went well, and all the courses I have been on regarding mobile telephony, I have saved the programs to use.
Until recently, the most commonly used program for intercepting cell phones was a program called "SS7", which is used by Danish police, as well as "NSA", which is probably the one that used the most, but the program that is able to search for a person, by searching for the person's (SMS - IP - PC - Voice calls - Voice recognition and Email.)
As well as being able to see what they had on their mobile phone / PC, and was there anything you want from it, or put somthing on their cell phone, you could do it without ever finding out.
"Network Voice Monitoring" (NVM)
It is some of the best software in the world today. It is amazing what it can and can do, and to understand it, here is some info:
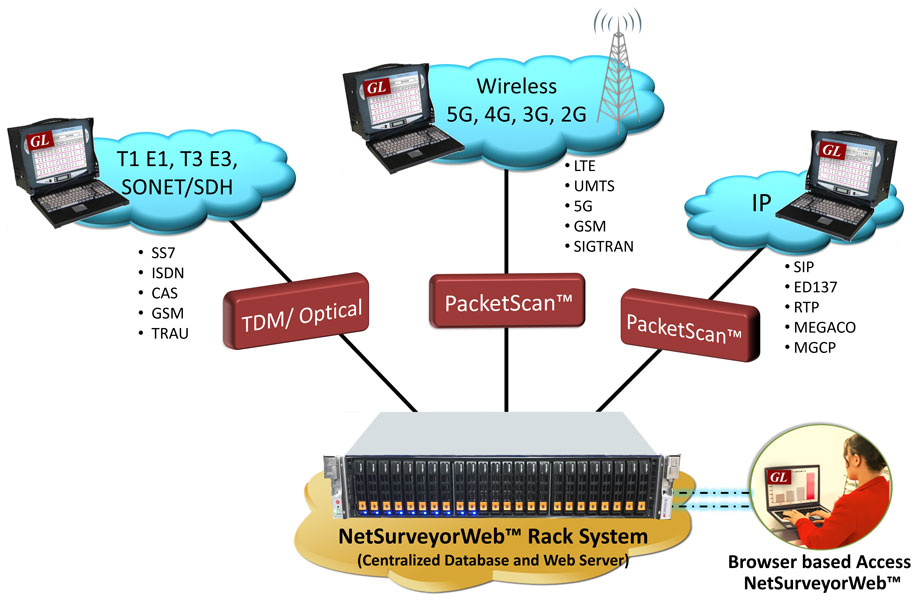
The essential elements of this monitoring system:
- VQuad together with associated hardware establishes calls or direct connections between variants of physical interfaces. The (recorded) voice files along with all events and measurements are automatically transferred from the individual nodes to the central location database.
- Mobile Phones, Bluetooth, Smartphones, Mobile Radio, WiMax, Wifi, Broadband 3G / 4G, Bluetooth, LTE, 2-wire analog (NB, WB FXO), T1 / E1 (PRI / CAS) and VoIP (SIP). The 4-wire analog interfaces (balanced, handsets, mobile radio) can be used in a non-automated way or in an automated way with additional customer-serviced call management functionality via external applications.
Then we have something called
"Indoor Tracking System" (ITS)
If someone is out there thinking, "We just go down the subway, they can't spy on us there." Unfortunately, you can, and pretty quickly.
If you want to track wireless voice quality when the user is underground where GPS is not available, there is the option of an ITS (Indoor Tracking System) setting in VQuad. This feature provides a map of the subway and allows the user to quickly identify the location and time of the call.
The ITS feature of VQuad is designed to perform VQT in remote and unreachable GPS signal locations (eg: underground). The ITS information (location, timestamp and JPG name) is stored in the VQT database using the VQuad Lat \ Long column.
As we always say, "They can run, but they can't hide".
Then we have arrived today, and with that said, I just want to say that I have been thinking a lot, really a lot about this, because it is what I personally use to keep track of certain people around the world, but as several have told me, of those I work with in this "gray world", that I had to put aside my personal problems, with certain people in World and elsewhere, because this is too important as it applies to everyone in Denmark and the rest of the world, and the only reason I tell what I know is because I know what they can do with people who have a cell phone.
And I say right away that you should not believe me, but even investigate what it is I am telling you, so that you can see for yourself that it is not a scams. So here we go ....
Everything goes back to "Edward Snowden" and to "The Deep Dark Web." There are documents coming out that have been hacked into from "The Dark WikiLeaks" about this current day.
They should have done it on September 20, 2018, but they said they were too busy with "Hurricane Florence", but that is some BS.
Then push a button and it becomes autonomous. It's already worked out with the cell phone companies, but because they're busy with "Hurricane Florence", they can't handle it right now.
There are a few things you may need to look up, there are things called "IMSI" catchers, (International Mobile Subscriber Identity) catchers, and these things are popping up all over the world they have argued after "Edward Snowden" come out with this bombshell, how they basically work and how they collect all our data.
We found out a lot more about these "IMSI" catchers, they basically intercept your phones and police stations around the world, including New York, which has basically admitted to using these "IMSI" prisoners since 2008 and not to mention you've ever seen the new stoplight that looks like cameras-like towers, it's the very advanced "IMSI" catchers in New York, so New York City is rigged for this all the time, and every time you can go past one, it will Catch hundreds of phone numbers, and hundreds of text messages, and no matter where they go, they are everywhere.
Now we come to the Top Secret shit, no one knows anything about, other than some very few people, including myself.
There is also another thing that has come out and it has not even been published yet, "VPO", (Variable Power On) is a "control chip" being put on phones and they haven't even told anyone about this but their excuse for this is that in an emergency you would be able to save your battery if you get caught on the mountainside for 127 hours then you can turn off your phone because if you keep the phone on , and waiting for someone to call or for them to find you, your phone may run out of power.
What they do is ping your phone and when they get close enough, your cell phone will turn on again and it would send a signal to turn your phone back on, even if your phone is off then they will have the opportunity to turn it back on and it would be "the good thing", "the positive thing" by using that chip.
This is already in most recent phones "Samsung Galaxy s7" and above, so check this out.
You have to look for small aircraft, "IMSI" catchers, they were not ready on September 20, as far as logistics smart, they will have our phones pinged, it should at least cover your phone camera front and rear , and if you can't turn off your cellphone for any reason, at least put tape over your camera.
Imagine every phone is pinged with something that could be info, it could be data, and whatever you have to press ok to clear it.
That is, this is a test of The President or whatever it says and then it says that nothing is needed, but you also have to press ok to make it.
At that point you will look straight at your phone, every single person in America, including we are talking about prepaid phones too, but that was not confirmed, but it`s now.
But they would be able to take a picture from the front or back of the one holding the phone.
And with the current "Face ID" that we have, it can actually go back to even the cheapest phones now, so we're talking about snatching pictures of people who really have never been on anything. (Very tender point).
The 5G
Through "The Deep Dark web" we are finding more and more what it is and it is very amazing with "5G" and all these new technologies coming out.
5G won't necessarily microwave you, but it will track your every move, even if you haven't turned on your phone.
What I would say is that it won't hurt you to switch off your phone just a little bit because if it's just a test and if they have a "VPO" then they can just turn on all your phones, but it would probably be published when people would freak out because their phones will be turned on again.
We may want to hear about this, but something like small planes, "FBI", "CIA", "NSA" and three letter agencies actually have these planes fly over us almost every single day and people can't even notice them .
But others can follow, too, because there are so many different agencies and they all use the same technologies.
What we are talking about are the "IMSI" catchers, which are small machines that you can build straight out of things you can buy from the shelves, and it will ping back to your phone and say, "Hi, I'm a cell phone tower" and then your phone will actually send all its info back.
They can control every single thing on your phone, and if you think about it, then the phone is for someone, their life.
Your story, everything you do, your GPS, your payments, everything you can see on a mobile phone, and believe me, I know, because I've done many times.
Here's something you can think about a little bit, to all of you who read what I have written, or next time you go to some of your friends and talk about it.
Just remember that it is "Samsung" with their "Samsung Galaxy S7". Take a good look at the name, is there something that pops into your eyes, if not, then get into this, "S7", the same as the most used interception program in the world, "SS7".
Also think about why all their new cell phones are called something like "S7", "S8", "S9".
And go one step further, with a program I've had for several years called "Weeping Angel".
This is the next generation "Samsung spy software", and is in use today in the World.
"Weeping Angel" is made to infect "Samsung smart TVs". The program is designed to break the malware through the internet and install itself on the TV.
Which then allows a person to take control of some of the TV's functions e.g. you can turn down the sound and light on the LED panel, making the TV look off.
But it's not off at all. Instead, the built-in microphone is active and can listen to what's happening in the room where the TV stands.
At the same time, they will also try to get the stored WiFi password and generally use the TV as a springboard for the rest of the network.
And I could keep going, because there are probably 20 of those kinds of programs that can do different things, against things you use everyday, day in and day out, 365 days a year, and then people don't understand why the government doing this, it`s all about control of the population.
Everyone who uses the Internet / mobile phone / SmartTV / Ipad / PC is monitored. If you think you are not spyed on, then you get a hint here.
Next time you go online, search for something you would normally never search. You can do it on Google or Facebook, once you have done this, you will log out as usual.
Then I will say with 100 percent certainty, that you will be offered some of the things you were looking for, the next time you log in, if it is not to be monitored, then I do not know what monitored is ....!
But I know all about how to monitor humans, whether it's me or "Sophia" who is an "AI" robot who just got "Saudi Arabia" robot "citizenship" that I wrote about on my blog called and the post is called "Blockchain - AI - Bitcoin", which is about how Bitcoin was made and by whom.
Be careful out there, you never know who is watching or listening.

Ingen kommentarer:
Send en kommentar