THE MOBLE PHONE
AND
THE SUVEILLANCE TOOL
IN
THE WORLD
By
Søren Nielsen
2019
People keep asking me, if I can`t write about what I know about surveillance and hacking.
I have worked with this for 25 years, so I've seen everything and tried everything, and especially, I have all the programs.
What People don`t understand that it`s the programming there is the source to all surveillance and hacking.
So if you know the programming, then you will understand how they can surveillance you.
The Mobile Phone.
There are 8.000.000.000 mobile phones in the world today. There are now around 4.3 billion mobile subscriptions in the world.
2 billion of the world's population has access to the Internet.
There are sold 2 billion TVs.
1.9 billion people have credit cards and 2.5 billion have a bank account.
Radio has so far been the world's largest mass media, with 3.9 billion FM devices in use.
But the mobile phone has now taken over the first place, around 65% of the world's population today has a mobile phone.
Every day, 3.2 million new mobiles are purchased worldwide.
DO YOU SEE THE PICTURE
So if you can control the phone companies, the tv stations, the newspapers and the internet, you have the world's best intelligence service.
Or like I all ways say, The worlds best Spy Tool to keep a eye on any one you what. I don`t mind that have that kind of programs, as long I also have it or understand what and who they do it, and I do....!
Because I know the way the program works and what it`s. And as long you don`t understand that, there is nothing you can do, to avoid to be hacket or spy on.
How do they do it...?
They working together with all the big companies, how invent these new things, and one then pays for them to invent something they can use against the population.
NSA is also engaged in hacking computers, smartphones and their networks. These operations are conducted by the Tailored Access Operations (TAO) division, which has been active since at least circa 1998.
In 2012, the NSA said more than 30,000 employees worked at Fort Meade and other facilities.
By 1990 this number had grown again to 75,000 military and civilian employees , of which 25,000 worked at the NSA headquarters.
What do they have of programs they can use against us.
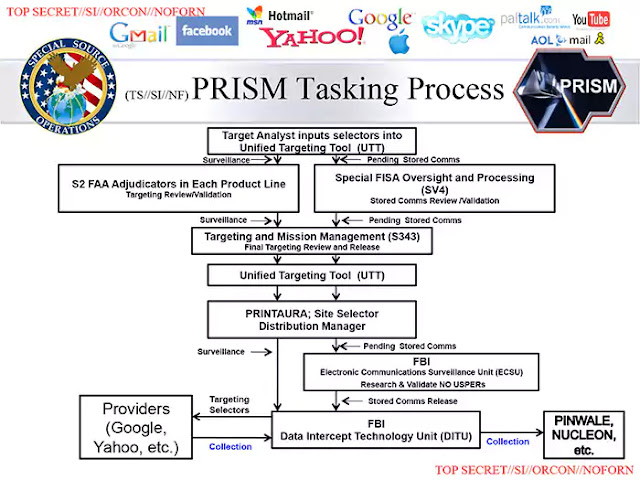
Their number 1 program is called : PRISM.



Under the PRISM program, which started in 2007, NSA gathers Internet communications from foreign targets from nine major U.S. Internet-based communication service providers: Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube and Apple.
Data gathered include email, video and voice chat, videos, photos, VoIP chats such as Skype, and file transfers.
This slide shows PRISM as only one part of the NSA’s system for electronic eavesdropping.
The "Upstream" program collects from the fiber-optic cable networks that carry much of the world’s Internet and phone data. The underlying map depicts the undersea cables that connect North America to the rest of the world.
This slide describes what happens when an NSA analyst "tasks" the PRISM system for information about a new surveillance target.
The request to add a new target is passed automatically to a supervisor who reviews the "selectors," or search terms. The supervisor must endorse the analyst's "reasonable belief," defined as 51 percent confidence, that the specified target is a foreign national who is overseas at the time of collection.
After communications information is acquired, the data are processed and analyzed by specialized systems that handle voice, text, video and "digital network information" that includes the locations and unique device signatures of targets.
The PRISM case notation format reflects the availability, confirmed by The Post's reporting, of real-time surveillance as well as stored content.
On April 5, according to this slide, there were 117,675 active surveillance targets in PRISM's counterterrorism database.
The slide does not show how many other Internet users, and among them how many Americans, have their communications collected "incidentally" during surveillance of those targets.
A slide briefing analysts at the National Security Agency about the program touts its effectiveness and features the logos of the companies involved.
This diagram shows how the bulk of the world’s electronic communications move through companies based in the United States.
PRISM program collects a wide range of data from the nine companies, although the details vary by provider.
This slide shows when each company joined the program, with Microsoft being the first, on Sept. 11, 2007, and Apple the most recent, in October 2012.
This was a very quick review of the PRISM program.
But it`s the same way that i work, as the PRISM work.
1: Targeting a “selector”
2: Checks and balances
3: Accessing private companies’ data
4: Data processed
5: What the analyst sees
6: Information collected
What I think is the most important thing to get hold of from the "selector" is,
1: Metadata
2: Login/ID
3: Photos
4: Social Networking
5: Stored data
6: Video
7: E-mails
8: Chat
9: Files
Most “metadata,” or records of the people, locations, equip- ment, times, dates and durations of communications, are collected in programs other than PRISM.
Some come from what NSA calls "Upstream":
Interception at the biggest junctions of the internet and telephone networks. Others come directly from telephone companies -- AT&T, Verizon Business Services and Sprint -- who keep detailed calling records.
The "metadata" results are processing by the NSA’s automated system code-named PRINTAURA. This system combines the roles of librarian and traffic cop. PRINTAURA sorts and dispatches the data stream through a complex sequence of systems that extract and process voice, text, video and metadata.
And that is here you get your info about what you what to know.
Personally, I almost use only the SS7 program, since people almost always have their mobile with them.
So there are no problems finding out what they are doing.
I think that today I have a database, with over 100,000 people. And it's from when they get up, what they eat, who they see and talk to, when did`t they have sex, and with who, do they have a car, ect ect ect.

What people don`t understand is that if you have any type of electronics in your home, you can be "hacked" and you can be "monitored".
If you not want to be exposed to any of the parts, so the only thing you can use is a, "Letter pigeon".
Now, you will get a insight, into how to monitor people.
The first thing you do is, (Where are they), but you always have an idea of where they are approx. Or you have an email, phone number, maybe an address.
But one thing you always have is "a name" and "a Place".
If you have a name and place, start with all social media or the internet, there is a program you can for free, there scan every social media, it`s about 80-90 website.
And if the person is on one of those website, then you will get some idea of what this person is doing, always.
Here should have been a list of programs, but chose not to do it because they should not know what one can do and can not do.
Overview
One of those things we use is called :
"Location based GSM/UMTS mobile terminals tracking system"
It`s a software platform is used for GSM/UMTS mobile tracking.
The system operation with up to 16 mobile operators.
For mobile location detection in most cases varies, but about 1500-5000 meters.
And it can go up to 1 000 location detection requests.
It is possible to set up multiple remote working places with Internet access or activate remote access from any authorized smart phone.
Operator can work from any place in the World using reliable connection through Internet, or with a separate dedicated data channel (for example, VSAT link).
It can detecting the mobile location by analyzing CGI (Cell Global Identifier) data received from the relevant mobile via GSM MAP SS7. (SS7 is NSA`s mobile spy program).
We use many programs, but in the start, we use 2 programs, and they are: "GSM/UMTS mobile tracking system" and "Mobile tracking and location system (GSM/UMTS Grabber)" number 2 program is for
"Cell phones location detection portable system thus significantly increasing the overall solution effectiveness."
"Cell phones location detection portable system thus significantly increasing the overall solution effectiveness."
Hardware and Software : Top Secret.
What can we see, when we find this people?
When we know were the are, we start to trace them, like this.
Web interface and is used to perform mobile terminal location search based on either (Mobile Station Integrated Services Digital Number) or (International Mobile Subscriber Identity).
And if you don`t understand what it`s. It`s your "Name" and "Mobil Number".
And then we start.
As you can see, when we have you number, we can follow you wherever you go.




This is the following information, we get on you.
1 : Request date and time, user ID
2 : Mobile terminal IMSI and CGI (Cell Global Identifier)
3 : Base station location and its coverage area.
4 : Mobile location data based on Google.


Here we see the person have been on 2 locations, we have the Time, date, Phone number, and how long he was there.
2. SS7 signaling code for interconnecting. Link to local GSM operator MSC (G.703 interface, 1 SS7 link).
3. GT for operator work place interconnection
4. SS7 and SCCP pre-settings at operator side.
5. A list of HLRs and their GTs (Global Title).
6. A list of MSISDN/IMSI ranges for each HLR.
And as you can see, The SS7 program from NSA, is still the best one, but not allways legal.














Ingen kommentarer:
Send en kommentar